








Smart Contract Security


Increase your security and protect your
users and money from attacks
users and money from attacks
Afraid your DeFi app
will get hacked?
Smart Contract
Security
for Ethereum, Solana and Ton ecosystems
Comprehensive testing to catch logic errors and
weaknesses in your code.
We expose critical vulnerabilities
before hackers do.
weaknesses in your code.
We expose critical vulnerabilities
before hackers do.
Comprehensive testing to catch logic errors and weaknesses in your code.
We expose critical vulnerabilities before hackers do.
We expose critical vulnerabilities before hackers do.
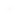












Audit methodology
Architecture Review
Description:
Stage goal:
- Discuss the found issues with developers
- Show remediations
- Write an initial report
Stage goal:
- Verify that all found issues are relevant
Static Analysis & Manual Review
Description:
Stage goal:
- Review the source code.
- Read the project's documentation
- Review the project’s architecture.
Stage goal:
- Build a good understanding of how the application works.
Description:
Stage goal:
- Help developers fix bugs
- Re-audit the updated code again
Stage goal:
- Double-check that the found vulnerabilities or bugs were fixed and were fixed correctly
Description:
Stage goal:
- The Client deploys the re-audited version of the code
- The final report is issued for the Client
Stage goal:
- Provide the Client with the final report that serves as security proof
Description:
Stage goal:
- Analyze the project's critical assets, resources and security requirements.
- Exploit the found weaknesses in a safe local environment (with the use of Hardhat and Foundry).
Stage goal:
- Identify vulnerabilities that are not listed in static analyzers that would likely be exploited by hackers
- Develop Proof of Concept (PoC)
Threat & Attack simulation
Report found vulnerabilities
Description:
Stage goal:
- Discuss the found issues with developers
- Show remediations
- Write an initial report
Stage goal:
- Verify that all found issues are relevant
Fix bugs & reaudit
Final
Certification
Description:
Stage goal:
- The Client deploys the re-audited version of the code
- The final report is issued for the Client
Stage goal:
- Provide the Client with the final report that serves as security proof
Description:
Stage goal:
- Manual check for vulnerabilities based on the auditor's checklist.
- Run static analyzers (i.e. Slither)
Stage goal:
- Identify and eliminate typical vulnerabilities (gas limit, replay, flash-loans attack, etc.)
Description:
Stage goal:
- Help developers fix bugs
- Re-audit the updated code again
Stage goal:
- Double-check that the found vulnerabilities or bugs were fixed and were fixed correctly
Description:
Stage goal:
- Analyze the project's critical assets, resources and security requirements.
- Exploit the found weaknesses in a safe local environment (with the use of Hardhat and Foundry).
Stage goal:
- Identify vulnerabilities that are not listed in static analyzers that would likely be exploited by hackers
- Develop Proof of Concept (PoC)
What our clients say about us


Pre-Audit Engagement
Services



Preliminary research
Audit scope discussion
Receiving project’s source code
Price and timeline agreement
Signing the contract
Conducting security audit

Use our cost calculator
To know how much your security will cost
The price depends on the number of lines and complexity of work.
We will provide the final cost after auditing the project and drawing up a work plan.
The price depends on the number of lines and complexity of work.
We will provide the final cost after auditing the project and drawing up a work plan.
Book for free
Services
Do you need an audit before release?
Education
Take a security training from BugBlow
Service
Use the Pentest service






For a quick response:
To get
a call back:
a call back:
Phone: +1 404 697 05 49
Email: hello@bugblow.com
Email: hello@bugblow.com
We work: Mon-Fri
From 10:00 to 23:00 (CST, Chicago)
From 10:00 to 23:00 (CST, Chicago)

Request a Smart Contract Audit
- to protect your users from data and financial losses;
- to improve your project’s reputation;
- to make your project more attractive for investors;
- to prevent security breaches
- to improve your project’s reputation;
- to make your project more attractive for investors;
- to prevent security breaches
FAQ
- Yes, all discussions and findings are confidential. Only after all bugs and vulnerabilities are fixed, with your permission we would like to publish our report, as it will serve as a proof of your increased security to your users and investors.
- During the audit, we stay in touch, ask developers questions, and share preliminary findings via your preferred communication channels.
- Think of it as tests to evaluate the found vulnerabilities. The attack simulation is conducted in a safe, local environment. It is needed to eliminate all false-positives findings.
Audit application form
Leverage security community


















